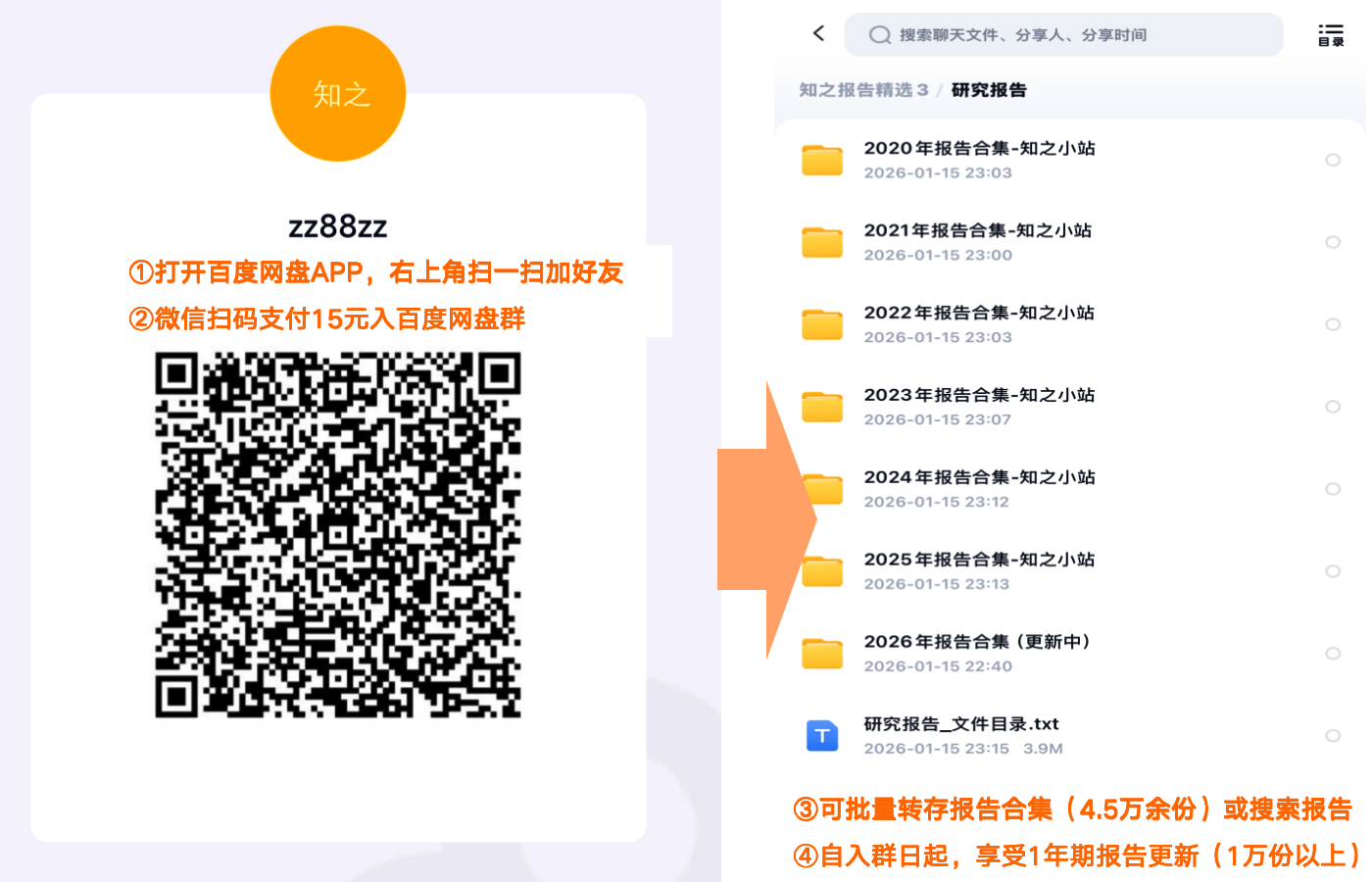
The challenge of integration is formidable, says Wilson. “Zero trust is not aswitch that you turn on,”but a philosophy of putting controls on data at the local level.A successful zero-trust strategy involves all vendors working together to ensure secure access to the applications or areas they’re responsible for.”A single large moat has become lots of little tiny moats everywhere,”Wilson says. The technical challenge is to build the moats deep enough to protect, but not so deep that applications can’t talk to one another as needed. “The segmentation piece is really, really hard,”he says.


本文来自知之小站
报告已上传百度网盘群,限时15元即可入群及获得1年期更新
(如无法加入或其他事宜可联系zzxz_88@163.com)